ITAR Compliance
Regarding ITAR compliance, unfortunately there is no official ITAR certification, but you can do the following to ensure your compliance:
- Registration with State Department’s Directorate of Defense Trade Controls (DDTC).
- Maintenance of records required by 22CR 5.
- Obtaining licenses or other approvals prior to making exports, temporary imports, or engaging in broker
ITAR/export compliance program
The Office of Defense Trade Controls Compliance “strongly advises” parties engaged in defense trade to establish and maintain an ITAR/export compliance program. Attached is a document from the State Department regarding compliance programs. In general, a good compliance program is:
- Clearly documented in writing
- Specific to your organization
- Regularly reviewed and updated
- Fully supported by your management team
Some of the Acumatica Cloud ERP capabilities that help it meet ITAR compliance includes:
- Its Help documentation is actually a Wiki that you can add your compliance program, organization structure, corporate policy, other information and procedures to, making them accessible to anyone on your team in a keyword searchable format.
- It has field level security that enables you control who has access to what information within Acumatica Cloud ERP.
- It has a built-in document management system that, coupled with its built-in security features, enables only authorized users to access documents to control access to sensitive data.
- The Engineering Change Control module and the QMS Suite provide additional supporting
- Management of regulated parts or products – Attributes (user-defined fields) can be attached to Acumatica Inventory items that specify whether the item is export controlled, which regulation and regulatory body covers the item, and the classification or rating within that schema which applies to it. Serial number tracking is native to Acumatica Cloud ERP.
- Assembly-level management – Acumatica can record the parts within an assembly and continue to track how/whether the assembly’s partners are covered by different export regulations and commodity jurisdictions, again through the use of Attributes.
- License application, usage reporting – Acumatica Cloud ERP has Monitoring built into it that gives its users (who have sufficient security access) visibility to their commercial transaction consumption, as well as other usage details. Acumatica Cloud ERP can be configured to automatically log users off the system after being inactive for a period of time that you designate.
- End-to-end encryption – Acumatica Cloud ERP uses digital certificates to store sensitive information in the database encrypted and to authenticate .pdf documents that are shared or sent electronically. All transmission is secure and encrypted using SSL technologies.
Other pertinent considerations:
- Denied Party Checks/Screening – Using a service such as Thomson Reuters ONESOURCE Denied Party Screening or a similar service, you screen your customers and suppliers against lists for restricted persons, embargoed countries, and companies that are owned by these denied entities.
- Vendor Validation – Using a solution such as Mekorma Vendor Validation for Accounts Payable Compliance in Acumatica, you can make sure you are not doing business with any enitify on the Office of Foreign Assets Control (OFAC) global sanctions list.
A final consideration is whether to deploy Acumatica Cloud ERP under their Software-as-a-Service (SaaS) public cloud subscription or under a private cloud subscription (PCS).
Public Cloud (SaaS)
Acumatica uses Amazon Web Services’ (AWS) public cloud to provision and manage its SaaS customers’ Acumatica Cloud ERP instances. Although the ITAR requirements are not explicitly violated by having your Acumatica Cloud ERP deployed under Acumatica’s SaaS subscription, there is not as much control over the location of the AWS data center and the specific individuals accessing the AWS datacenter for the SaaS offering as could be available under the PCS offering.
Private Cloud (PCS)
Acumatica’s customers with PCS subscriptions are able to choose where to deploy their Acumatica Cloud ERP instances. To maintain ITAR compliance, they can deploy their Acumatica Cloud ERP instance on-premise with appropriate security measures and processes in place.
They can also choose to deploy their Acumatica Cloud ERP instance in a private cloud that is capable of supporting their ITAR obligations and compliance program. Examples of ITAR-compliant data centers are Microsoft Azure for Government and AWS GovCloud. In addition to the capabilities that the Microsoft Azure and Amazon Web Services (AWS) public cloud data centers provide, these services are guaranteed to be managed solely by U.S. Persons in U.S. locations and that all customer data within these clouds are treated as ITAR data.
FedRAMP Compliance
As you can see below, the standard AWS US East/West Regions if FedRAMP Moderate, while the AWS GovCloud is FedRAMP High:
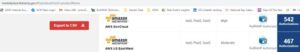
FedRAMP compliant, independent of whether it is deployed as a SaaS subscription on Acumatica’s public cloud that is hosted by Amazon Web Services or if it is deployed as a PCS subscription on your premise or a private cloud.
What FedRAMP Is
As you probably know, the Federal Risk and Authorization Management Program (FedRAMP) is a program run by the U.S. federal government to help cloud service providers bid on government contracts. Simply put, FedRAMP helps such providers achieve minimum standards of cybersecurity, so they can sell their cloud service offerings to federal government agencies more efficiently. All cloud service providers (CSPs) must achieve FedRAMP authorization to be able to contract with federal agencies. The authorization serves as a “seal of approval”, so individual agencies don’t need to re-perform an entirely new security assessment for each CSP that might come along.
FedRAMP Compliance – Data & Security
Acumatica Cloud ERP’s data storage and security complies with SOC 3, FEDRAMP, FIPS 140-2, GDPR and other domestic and international compliance mandates independent of whether it is deployed as a SaaS subscription on Acumatica’s public cloud that is hosted by Amazon Web Services or if it is deployed as a PCS subscription on your premise or a private cloud.
FedRAMP Compliance – Cloud Service Offering (CSO)
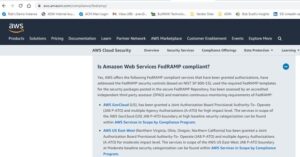
Any cloud provider looking to sell its cloud service offering (CSO) to federal agencies must achieve FedRAMP compliance by adhering to the security requirements outlined in NIST Special Publication 800-53. Many public CSPs are FedRAMP compliant and authorized. AWS is one. Click here to read more about AWS and FedRAMP, which states that, as of May 21, 2013, both Amazon Web Services’ U.S. AWS Regions (i.e., the public cloud that Acumatica uses for its SaaS subscribers’ Acumatica Cloud ERP instances) and AWS GovCloud (which, as I mentioned below, is an option for the PCS subscribers to deploy their Acumatica Cloud ERP instances on) are FedRAMP certified.
Another good page to reference regarding this is from AWS itself at https://aws.amazon.com/compliance/fedramp/. Here is a snapshot from that page:
How Users Connect to Acumatica Cloud ERP
Users will connect to Acumatica Cloud ERP from devices (desktop computers, laptop computers, tablet computers, smartphones, smart watches and/or other smart devices) that are approved by your compliance program using the same browser-based or mobile-based (iOS or Android) interface and log-in process, independent of where Acumatica Cloud ERP is deployed.
Authentication Capabilities
In addition to the login security within Acumatica Cloud ERP, it also has native multi-factor authentication capabilities that can be implemented to provide multi-factor authentication via email, SMS, or push notification.
Advanced Authentication is an optional addon module that enables external identify authentication by integrating with Google or Microsoft identity providers, Microsoft Active Directory, or any OpenID Connect provider for single sign on (SSO) and/or multi-factor authentication to provide centralized management of user access.

